The news of the CPU vulnerabilities in the latest period of time can be astonishing. One of the most unlikely and most inadmissible key devices actually has hardware flaws! The busiest thing for PC makers these days is the introduction of patches that use software to make up for hardware bugs. Moreover, these measures will also lead to reduced CPU performance. But what exactly does this loophole affect? Do you really need to worry about this?

The loophole is true but not afraid
Vulnerability exists. This is true, but you don't need to worry about it. This has been confirmed to affect the hardware defects of almost the CPU for more than a decade, but the technical details of this loophole are not ) Public to the public.
From last year, Google’s Project Zero team discovered some chip-level vulnerabilities caused by Speculative Execution, “Spectre†(variants 1 and 2 variants: CVE-2017-5753 and CVE-2017-5715) and "Meltdown" (Variant 3: CVE-2017-5754), these three vulnerabilities are caused by inherent architectural design flaws that allow non-privileged users to access system memory and thus read sensitive information. Simply speaking, these vulnerabilities can allow malicious programs to obtain sensitive content stored in the core memory, such as memory data that can cause hackers to access the personal computer, including user account passwords, application files, and file caches.
After further confirmation (see "News Tea Fan") including Intel, AMD, and ARM's CPU are on the "blacklist", which means that whether it is Windows, Linux, Mac system or mobile Android, there are potential Security threats. However, it is only a "potential threat."
CPU authority what ghost?
Most modern CPU architectures have some form of protection ring. Each ring has different levels of protection and can call different CPU resource levels. For the Intel X86 CPU with the first exposure problem, he has four levels of Ring0, Ring1, Ring2, and Ring3, and one Ring-3 level of authority.
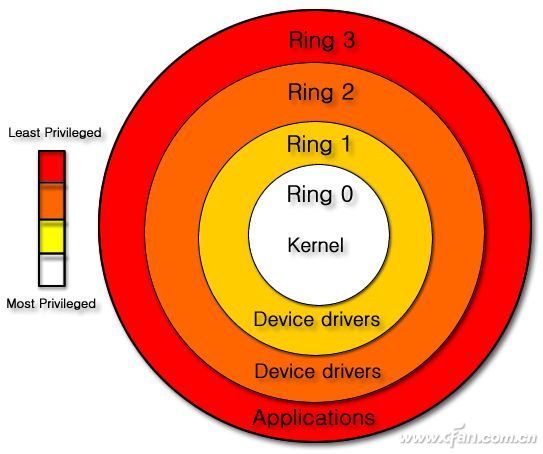
Common operating systems such as Windows, Linux, Android, iOS, etc. operating systems do not use all the various levels of permissions, but only use a part of them. In Windows terms it uses 3 Rings levels: Ring 0 is for kernel code and drivers, Ring 2 is for some privileged code (such as user programs that require I/O permissions), and Ring 3 is for non-privilege Code (almost all applications are at this level).
In all instructions of the CPU, some instructions are very dangerous. If they are used wrong, it will cause the system to crash. For example: clear memory data, set the clock, etc. If the application is free to call these instructions belonging to different permissions, then the system will appear a variety of unsolved problems. Therefore, the CPU divides instructions into privileged instructions and non-privileged instructions. For those dangerous instructions, only the operating system and its related modules are allowed to use. Ordinary applications can only use those instructions that do not cause disaster. For example, if an ordinary application attempts to execute the Ring 0 instruction, Windows will display an "illegal instruction" error message. The most widely-spread CPU vulnerability is that it can directly call Ring 0 permission through illegal instructions! So it is indeed dangerous from a security perspective. The only good news is that no one has yet achieved such an attack.
The problem that Intel has exposed recently is more than this. Do you remember another loophole in Intel's other days? The panic caused by the ME management engine is even more terrible than this one (this time it was wide and last time it was a big hazard): The ME management engine in the Intel CPU for the last three years is based on the Ring -3 authority - this right is supreme , it does not depend on any system, plainly is a complete system inside the CPU! It can be said that if this loophole is mastered by a technical attack, your computer will not belong to you technically because the authority used by the ME management engine is too high to be a native operating system in the CPU! Of course, there are corresponding patches, and only affect the 4th generation Core Duo products. The range is much smaller than this.
Obviously, CPU rights management is very important, but Xiao Bian feels that ordinary users do not have to worry about, and even Xiaobian think at this stage ordinary users own computers are not necessary to patch (business companies, government and enterprise units is very necessary! Security is important. The technical details of these vulnerabilities will not be announced. This means that we will not face huge security threats in a short period of time. In particular, home computers must consider the part of performance loss, rather than wait and see.

48V Battery Pack ,Switch Battery Pack,Portable Lithium Battery Pack,48V Lithium Ion Battery Pack
Zhejiang Casnovo Materials Co., Ltd. , https://www.casnovo-new-energy.com
